Secure SCADA
How Vulnerable Is Your System and What You Can Do About It?
- The Threat
- Software Security
- Hardware Security
- End-to-end Security and First steps
The Threat to SCADA and Automation
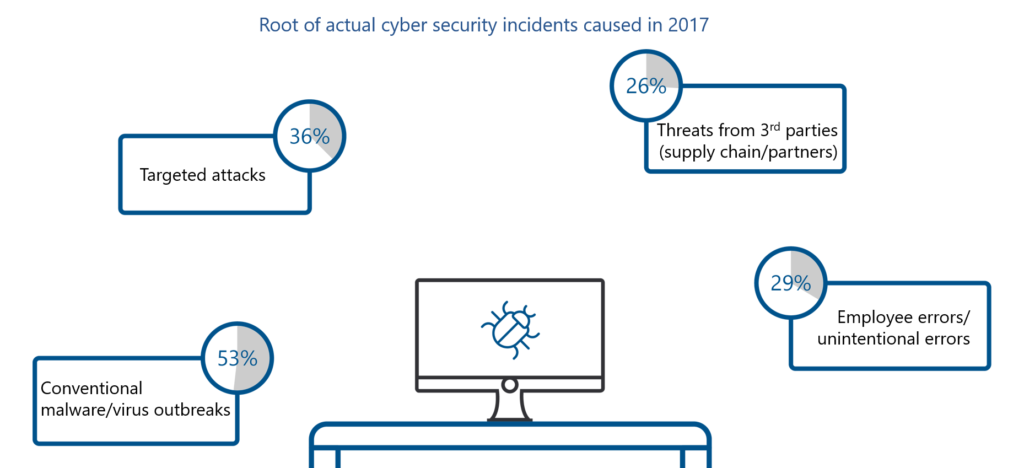
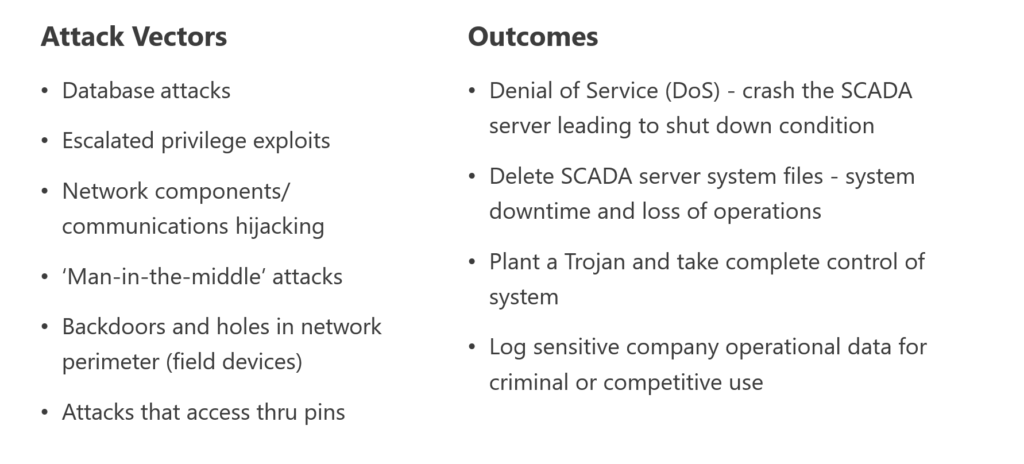
What’s the Exposure?
Stuxnet – An Extreme Case

What You Want in a “Secure” System
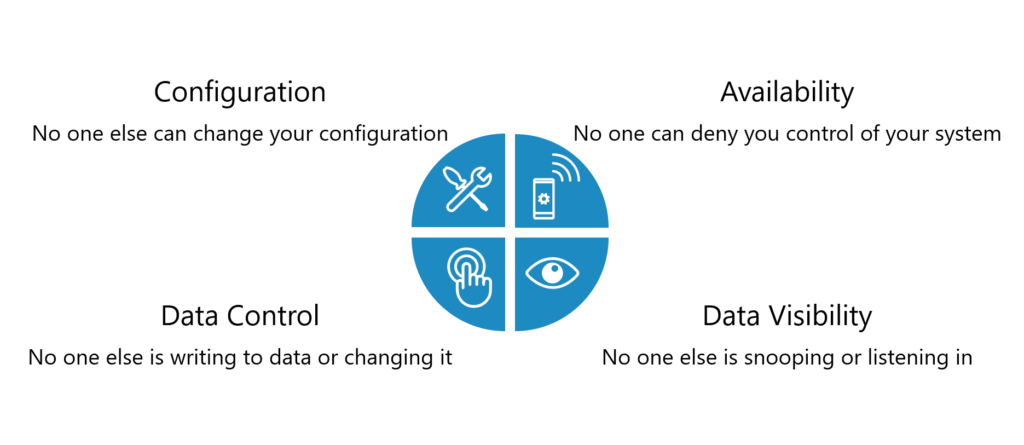

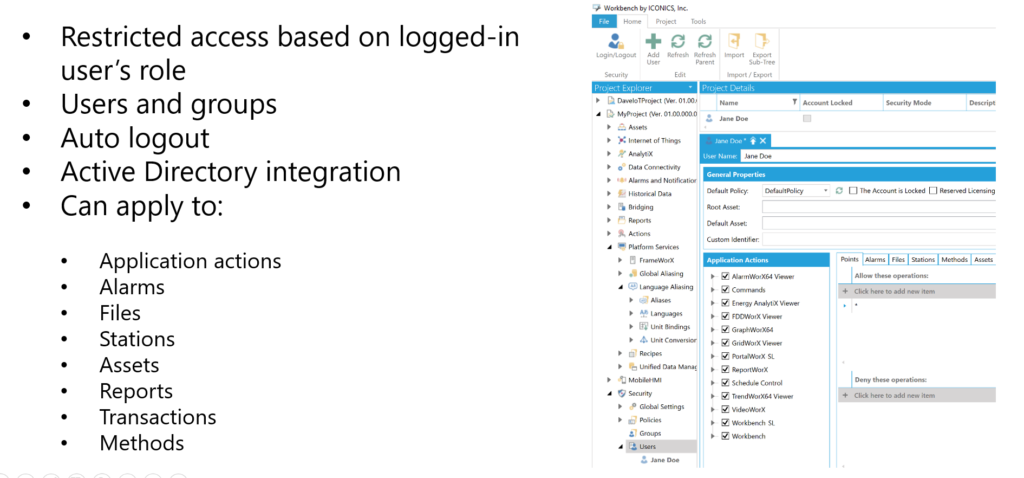
ICONICS Security Server
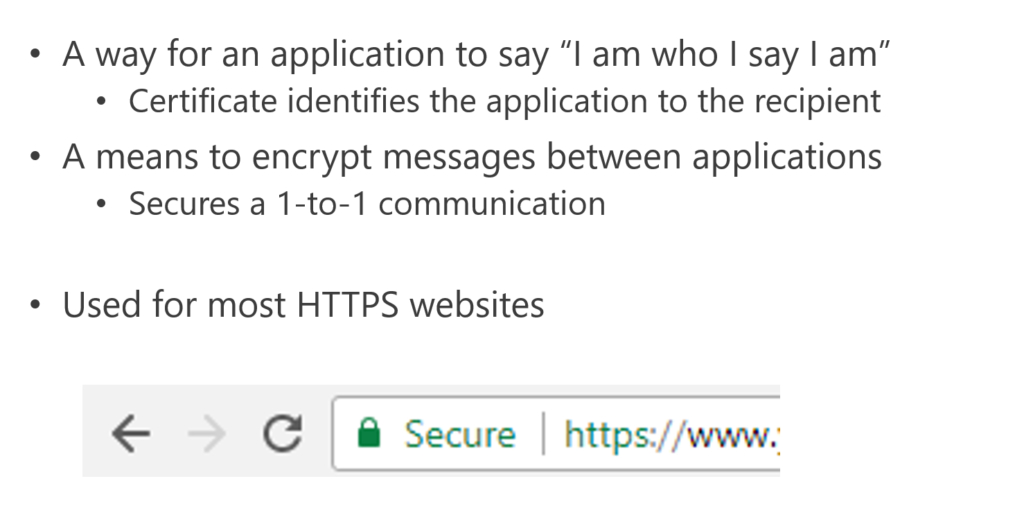
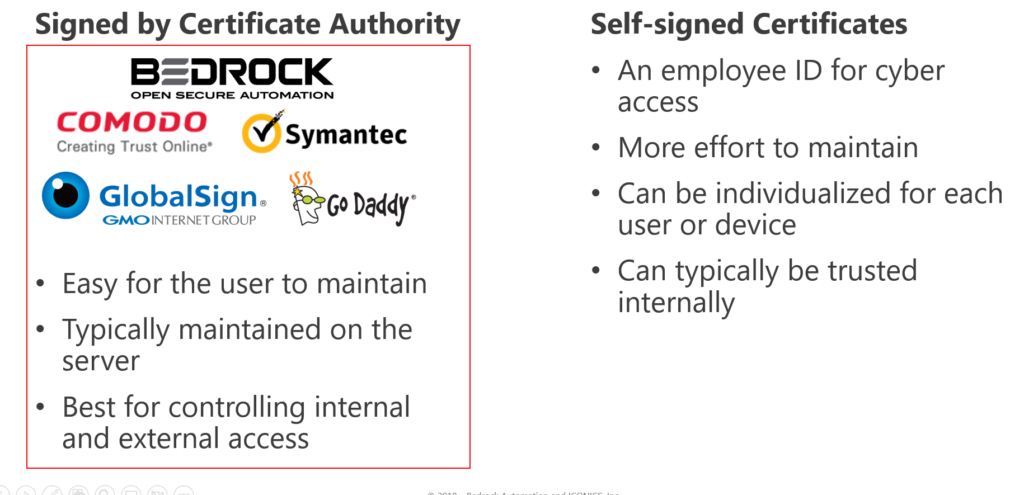
What Are Certificates?
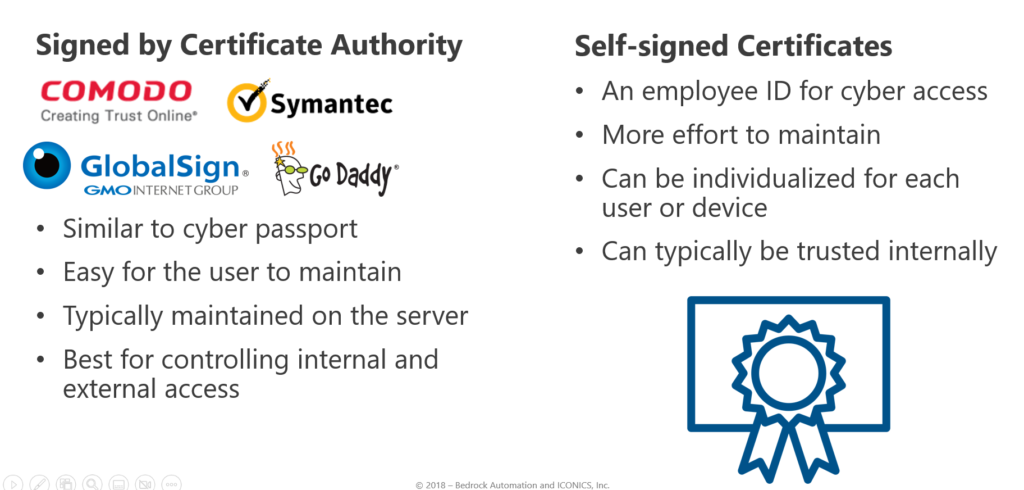
Types of Certificates
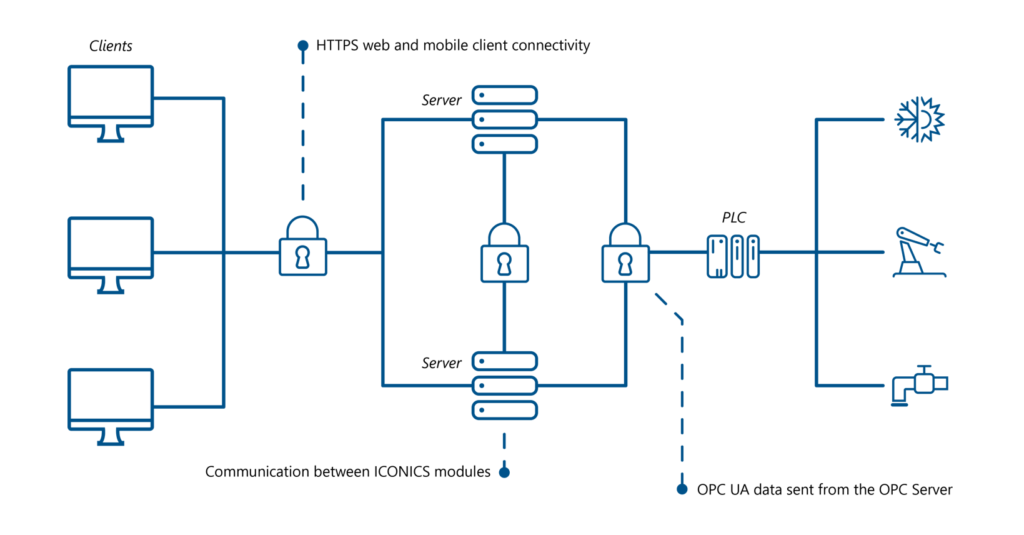
Using Certificates in Secure SCADA

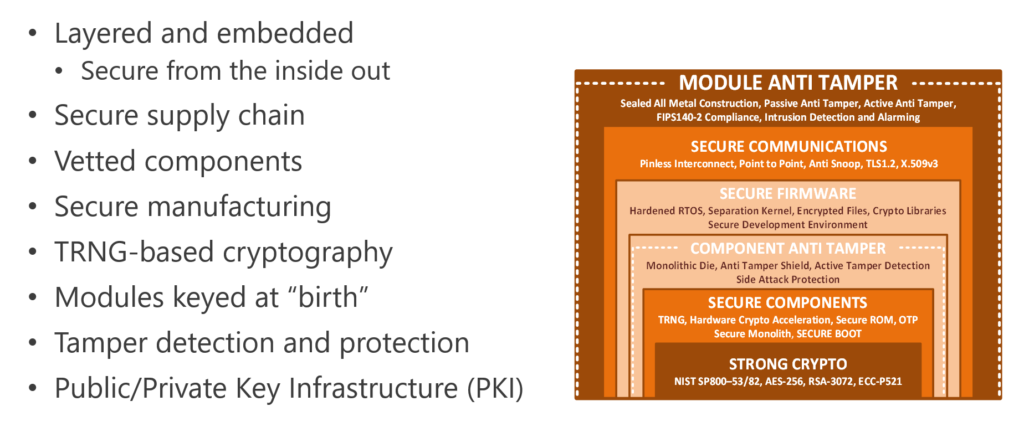
Hardware-based Defense
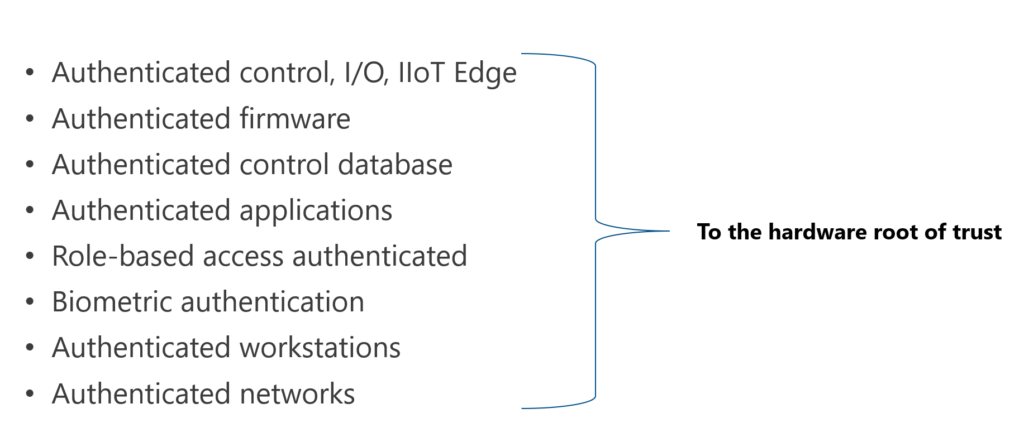
Intrinsic ICS Defense
Types of Certificates
Bedrock CA
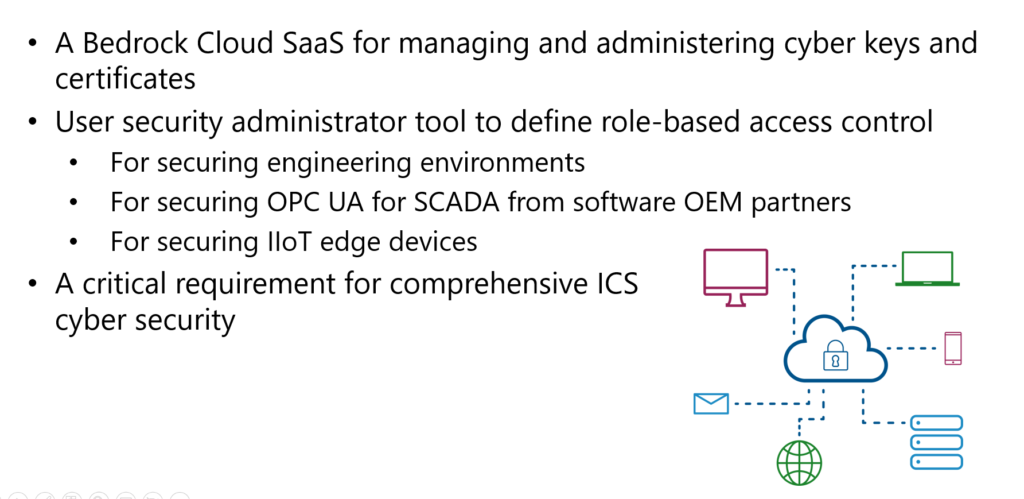

Leveraging Intrinsic Security – Cybershield

Holistic Security
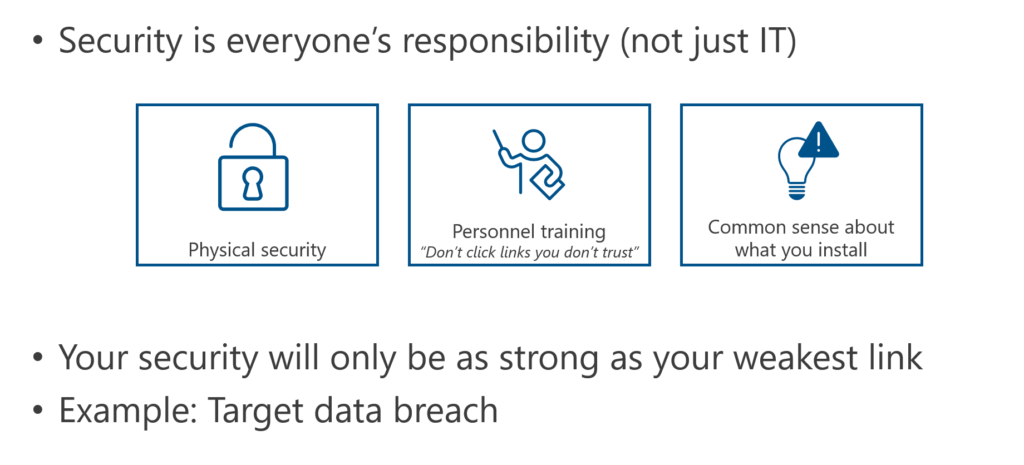
Opportunities for Protection
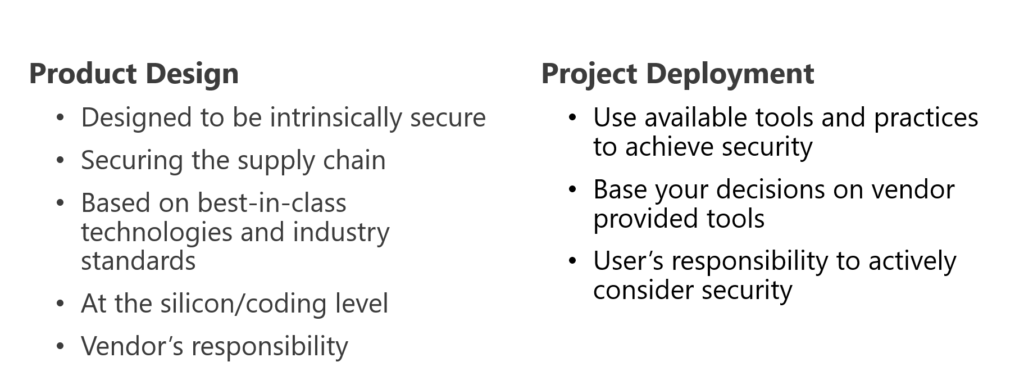
What You Can Do to Secure Your PLC/DCS
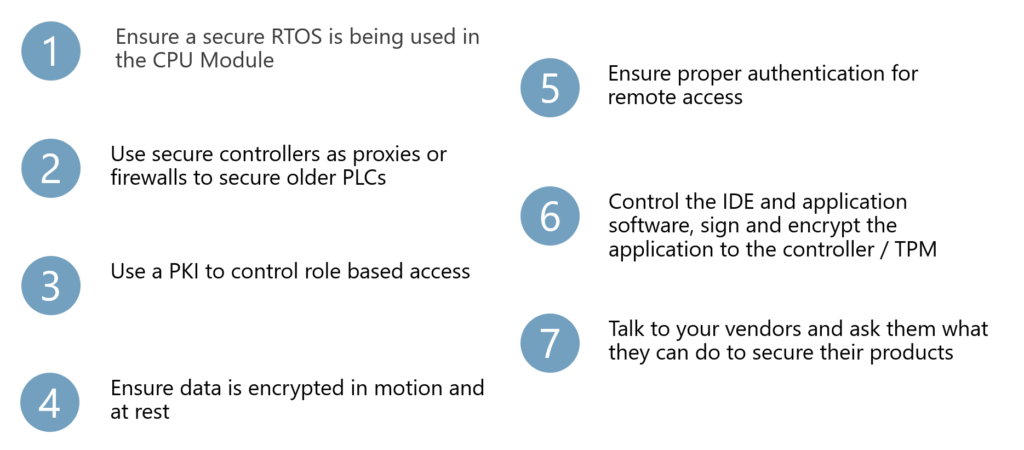
What You Can Do to Secure Your SCADA
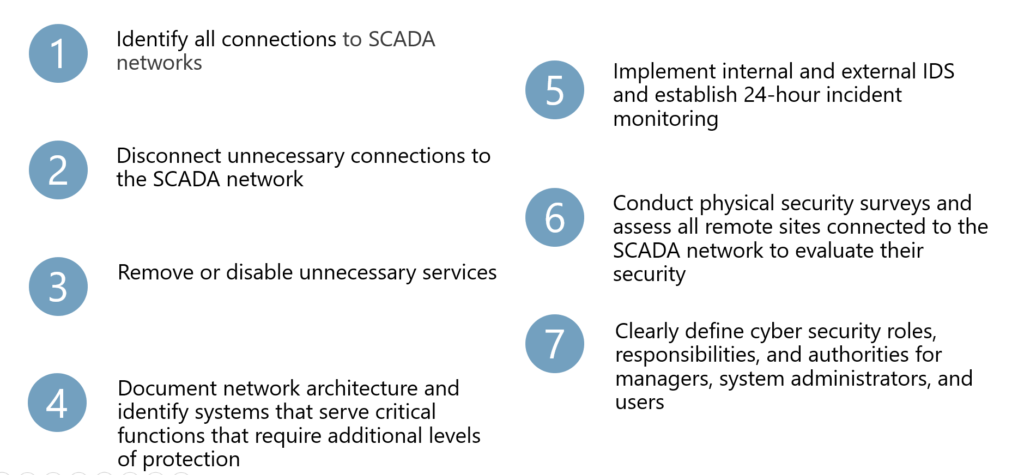
First Steps
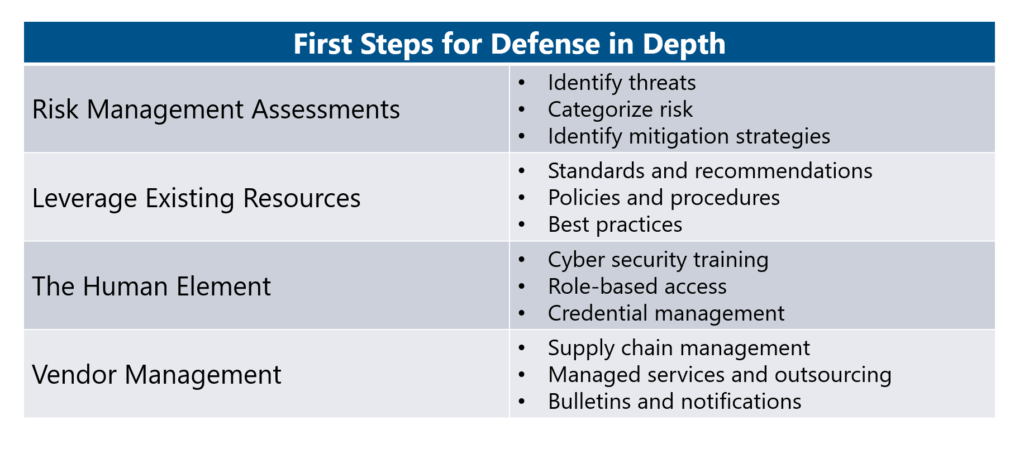
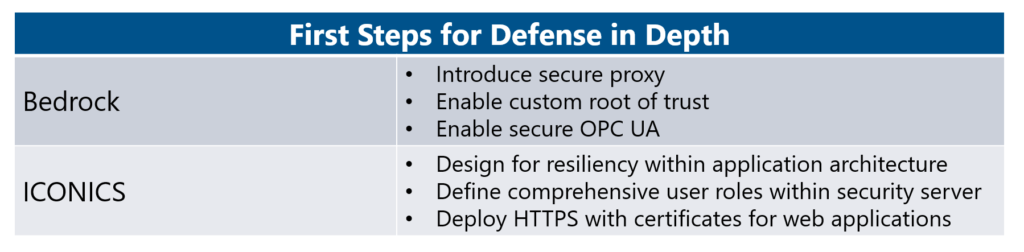
First Steps with ICONICS and Bedrock
Takeaways

Conclusion